Stop Shouting into the Void: Why CTI Teams Need Feedback Loops

Note: This is not a study. It reflects my personal view on the importance of the feedback loop.
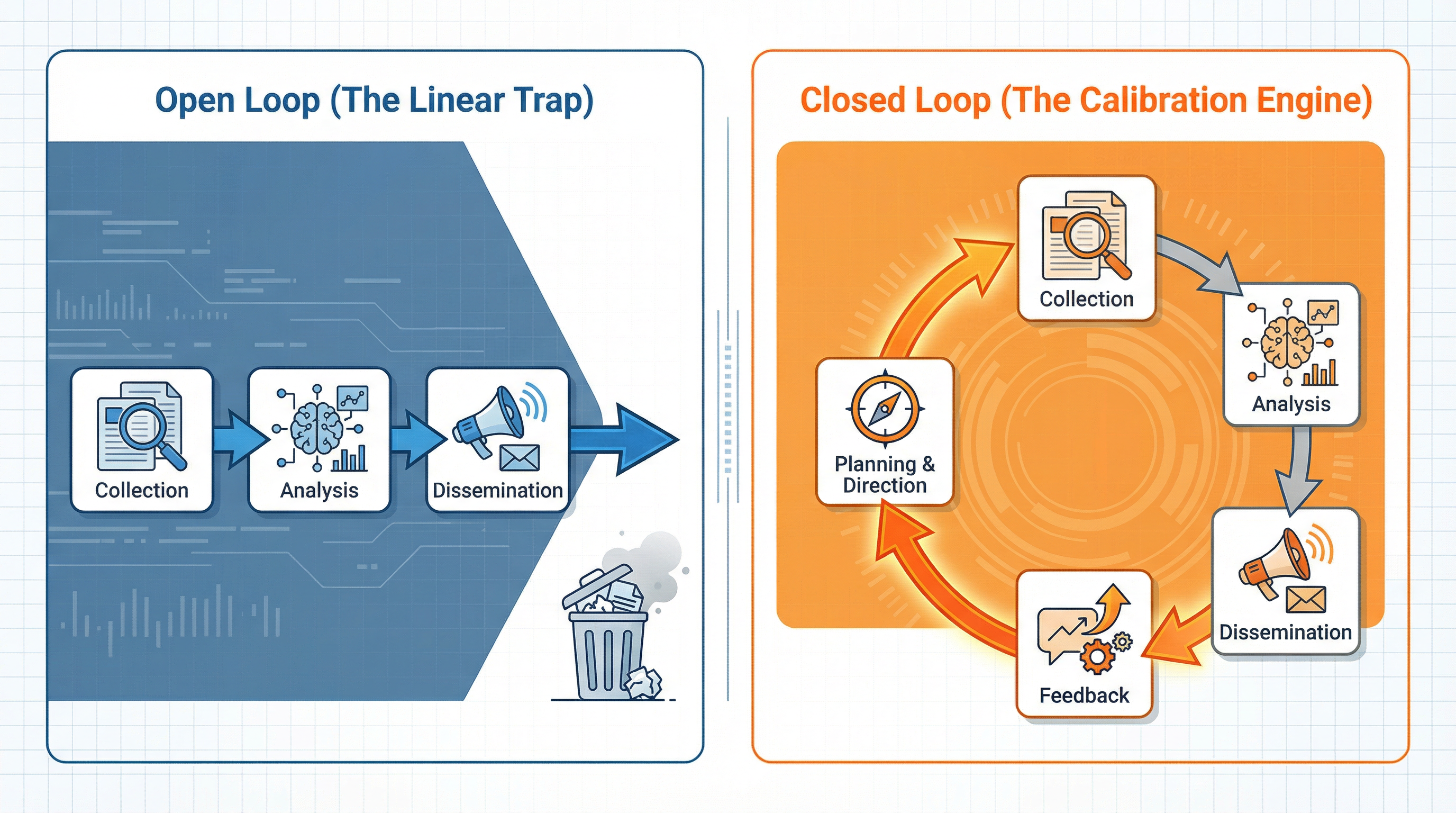
We call it the Intelligence Cycle. It is not a straight line. It does not terminate at an inbox.
To a tired analyst, the "Send" button looks like a victory flag. In a tactical crisis, it is. Speed counts when the fire is burning.
But for long-term programme maturity, this is a dangerous illusion.
Sending the report is not the outcome. It is just an output. When we stop at dissemination, we make a massive assumption. We assume that delivery equals value.
The Vacuum of Assumptions
We assume the CISO prioritized our report over their hundred other unread emails.
We assume the SOC can use our PDF, not knowing they need a CSV file to actually upload the indicators into the firewall.
We assume the intelligence arrived in time to impact a decision.
Usually, these are just guesses.
Engineers know that open-loop control systems cannot correct errors. Cyber Threat Intelligence is the same. Without an explicit feedback mechanism, we operate in a vacuum. We guess what matters to the business. We guess if our format works.
This neglect causes Strategic Drift. The output slowly moves away from stakeholder needs. The team stops being an intelligence unit and becomes a news agency. We produce interesting content instead of actionable intelligence. Eventually, stakeholders stop seeing our reports. They see it as spam.
The CTI Value Matrix
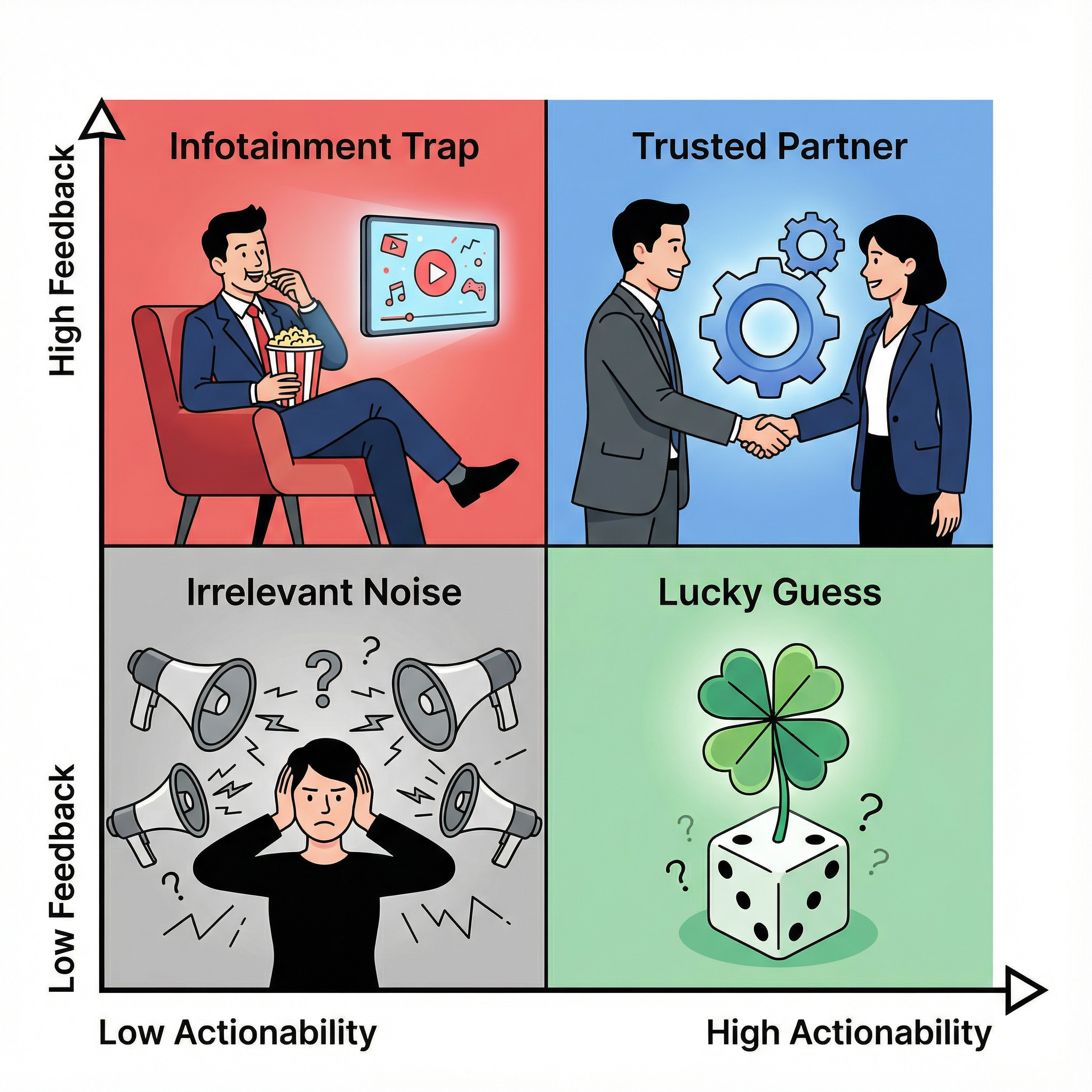
To measure the health of an intelligence programme, we can map our output against: Actionability (Utility) and Feedback (Validation).
Most teams get stuck in one of three failure modes:
1. The Infotainment Trap (High Feedback / Low Actionability): You produce a deep dive on a threat irrelevant to your sector. The CISO replies, "Excellent analysis!" because it was interesting. But since the business has no exposure, nothing changes. You provided entertainment, not risk reduction.
2. The Lucky Guess (Low Feedback / High Actionability): You block a threat, but you never get to validate it. You cannot replicate this win because it was chance, not calibration. Eventually, your luck runs out.
3. Irrelevant Noise (Low Feedback / Low Actionability): Generic news summaries. This teaches your stakeholders to auto-archive your emails without reading them.
The goal is the top right: The Trusted Partner. You provide high-fidelity data, and the stakeholder validates it. You stop guessing and start building what they use.
Force the Calibration
Here is how teams can close the gap without becoming a burden:
1. Direct Interaction: Email is passive. Deliver critical strategic intelligence face-to-face (if possible). The immediate reaction reveals if the message landed or if it confused the audience. You cannot read body language in an inbox.
2. Low-Friction Verification: Don't assign homework. Keep requests binary. A simple "Did we see this hash?" is enough. It turns a monologue into a dialogue. If they are too busy to check, the threat may not be their priority. That is a valid signal.
3. The "So What?" Gate: Enforce a strict pre-send rule. Every intelligence product must answer exactly what the stakeholder should do next. If a report ends with "Monitor for activity," it is likely noise. Do not hit send until the "So What?" is concrete.
Conclusion
Intelligence is a cycle for a reason. A loop improves with every turn. CTI Analysts must prioritise precision over volume. By actively seeking feedback, we stop broadcasting and start acting as true advisors.