Malicious Infrastructure Hunting: Part 0: The Foundation

This is a three-part series where we'll talk about malicious infrastructure hunting! Over the next few posts, I’m going to show you how to get started using nothing but free tools.
-
Part 0 (You are here): A short primer on what malicious infrastructure, why it matters, and what responsible OSINT is. This is a foundational briefing where we won't dive into specific techniques or tools, but set the stage for future chapters.
-
Part 1: The Hunter's Toolkit: Here, we will discover which data points are important to us. We will also introduce some free but essential tools into our workflow.
-
Part 2: The Art of the Pivot: The hunt starts here. We'll map out malicious infrastructure and pivot off simple indicators.
-
Part 3: Infrastructure Clustering: Lastly, we will learn how to do intermediate pivoting and analysis to connect the dots and find clusters of malicious activity.
Introduction: Shifting Your Focus Outward
Traditionally, Threat Hunting is a practice in which the blue team proactively searches for and uncovers threats within their own networks. Threat Hunters operate under an assumption that attackers are already operating undetected within the environment. This allows defenders to discover previously undetected threats and to reduce the length of time a threat actor dwells within their networks.
But what if you could catch attackers before they even launch their attacks? That’s the core idea behind adversary infrastructure hunting.
Instead of looking inward, we shift our focus outward to the global internet. It's the proactive work of finding, mapping, and tracking the domains, servers, and other online assets that attackers assemble for their operations. By applying the same disciplined hunting principles to the open internet, we can spot attacks being staged, anticipate an attacker's next move, and shift from a reactive, "firefighting" mode to a proactive one.
After all, threat actors rarely use a single computer; they build out a network of infrastructure to run their C2 servers and Phishing site. By finding and watching these external pieces, we can anticipate their next move and reduce the amount of time an attacker goes undetected.
The Anatomy of Malicious Infrastructure

So, what constitutes malicious infrastructure? It's a collection of digital assets an attacker pulls together to achieve their operational objectives. Let's look at some of the more common pieces.
-
C2 Servers: The control centre of threat actors. From these servers, they send commands to infected machines to bring them closer to their objectives such as exfiltration of sensitive information or even deploy ransomware. Certain famous C2 Frameworks include Cobalt Strike, Metasploit and Sliver.
-
Phishing Websites: You’ve seen these before. They’re the fake websites that pretend to be your bank or a login page for your organization's Microsoft 365. This is designed to trick people into disclosing sensitive information or to download malware.
-
Malware Hosting Sites & Staging Servers: These servers are used to host and hand out malware, exploits, and other malicious tools. Attackers often use "bulletproof hosting" providers, which are services that look the other way on illegal activity, making them very difficult to shut down.
-
Redirectors: A redirector is a simple server that forwards traffic from an infected machine to the real C2 server. If a security analyst traces the traffic, they only find the disposable redirector, not the C2 server behind it. The attacker can easily sacrifice the redirector while keeping their main server safe.
A smart attacker will never bunch all of these pieces onto a single server. For operational security (OPSEC), they usually keep their setup compartmentalized and separate. In case one of their pieces gets discovered and burnt, the rest of their infrastructure can remain intact and operational.
The Hunter's Mindset
The same model that guides traditional Threat Hunters will also be applied to hunting on the open internet. This process starts with the right mindset: assume you're already a target and work backward to find the proof.
These familiar hunting models are our primary ways to kick off an external investigation:
-
Hypothesis-Driven: You start with a "what if...?" question based on intelligence or your environment. For example, "I suspect that attackers might be setting up domains to phish our employees." Then you go hunting for evidence to prove or disprove it.
-
Indicator-Driven: Using a clue, like a malicious IP address, a suspicious domain name or a malware hash, we pivot from it and try to discover if there are any other connections to it.
-
Analytics-Driven: By using existing data, we start looking for anomalies, like a single server suddenly hosting dozens of brand-new, unrelated domains.
The OODA Loop
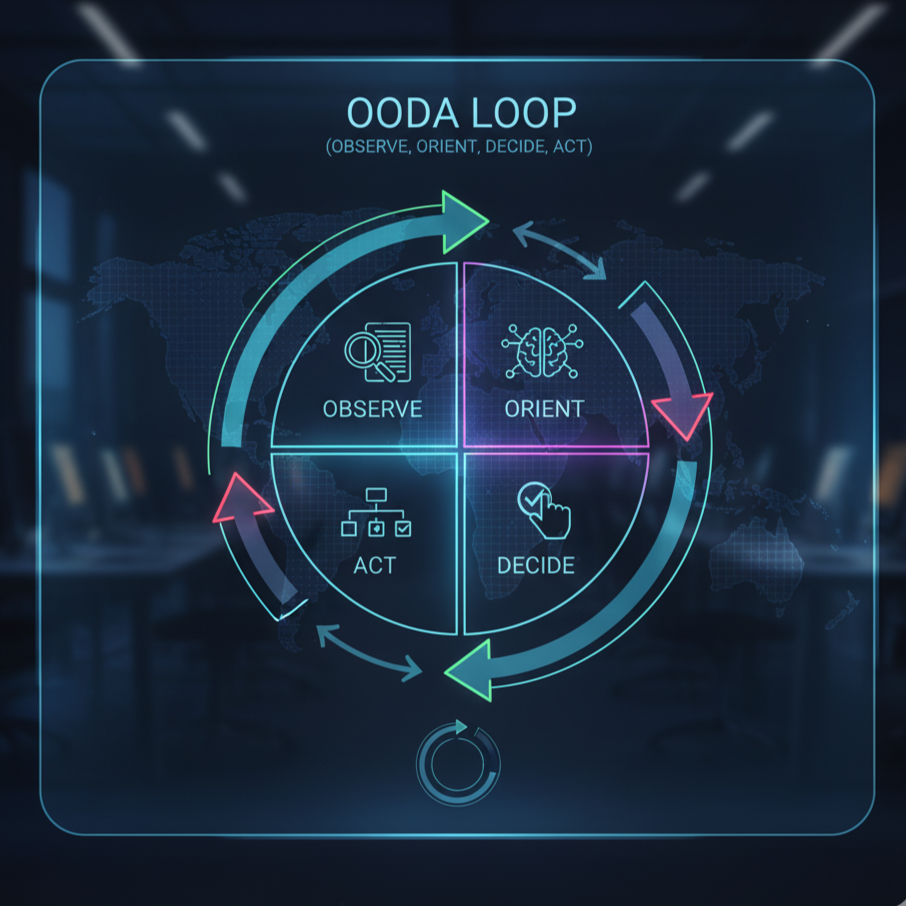
A great mental model used by the Intelligence Community is the OODA loop (Observe, Orient, Decide, Act). The power lies in allowing you to make better decisions in confusing and chaotic situations.
Instead of just a simple checklist, think of it as a continuous cycle for processing information.
-
Observe: You observe a raw piece of data or a clue. It could be a suspicious domain name found in a log, an IP address from a threat feed, or an unusual detail on an TLS certificate.
-
Orient: To orient is to combine this observation with everything you already know such as your professional experience, understanding of attacker tradecraft, and the threat intelligence currently on hand.
-
Decide: Choose a specific course of action based on your current understanding of the situation. This step is designed to test your theory or gather a specific piece of information. For example, "Based on that weird TLS certificate, I'll decide to search for other certificates that share its unique serial number."
-
Act: This is the execution. You act on your decision. You run the search, you query the database, you pivot to a new data point. The result of your action immediately becomes your next observation.
Each action feeds a new observation, forcing you to constantly re-orient your understanding and make a new decision.
Ethical Compass: Legal and Responsible OSINT
Before we begin, I would like to talk a little about the ethical part of OSINT, which is what this method of hunting relies on. But "publicly available" information doesn't mean you can do whatever you want with it.
Some things to note:
-
Legal does not mean Ethical: Just because you can does not mean you should.
-
Verify Everything: Unverified information is just a rumour. Before you act on any piece of data, verify it against another source. A single data point is only a lead, and not necessarily concrete proof.
-
Stick to passive data collection: Do not cross the line by actively poking a target's system. Besides causing potentially real damages and legal implications, you might accidentally tip off the threat actor that you are investigating.
Misrepresenting your findings will destroy your credibility and could have serious tangible repercussions. If you can't be trusted to run proper investigations, you're as good as useless.
What's Next?
And that's Part 0 of our Adversary Hunting series. This was a short introduction to set the stage. We've covered the "what" and the "why" of adversary infrastructure hunting, along with the mindset required to do it right.
In the next post, we'll roll up our sleeves and get practical. In our Part 1, we will start building our Hunter's Toolkit and dive into the actual tools and methods you can use in your own investigations.